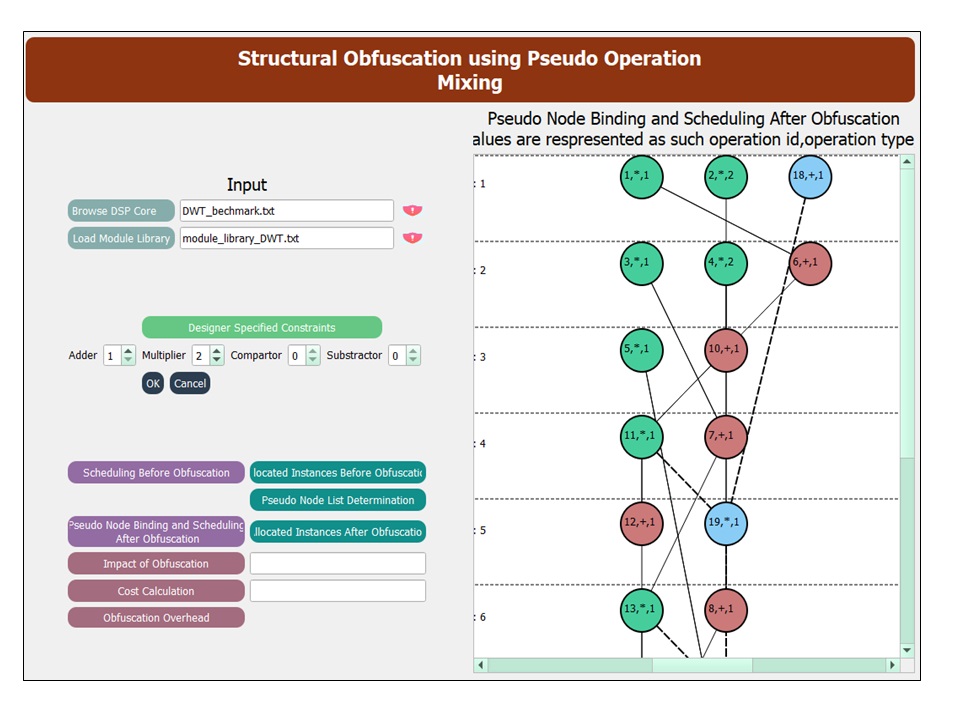
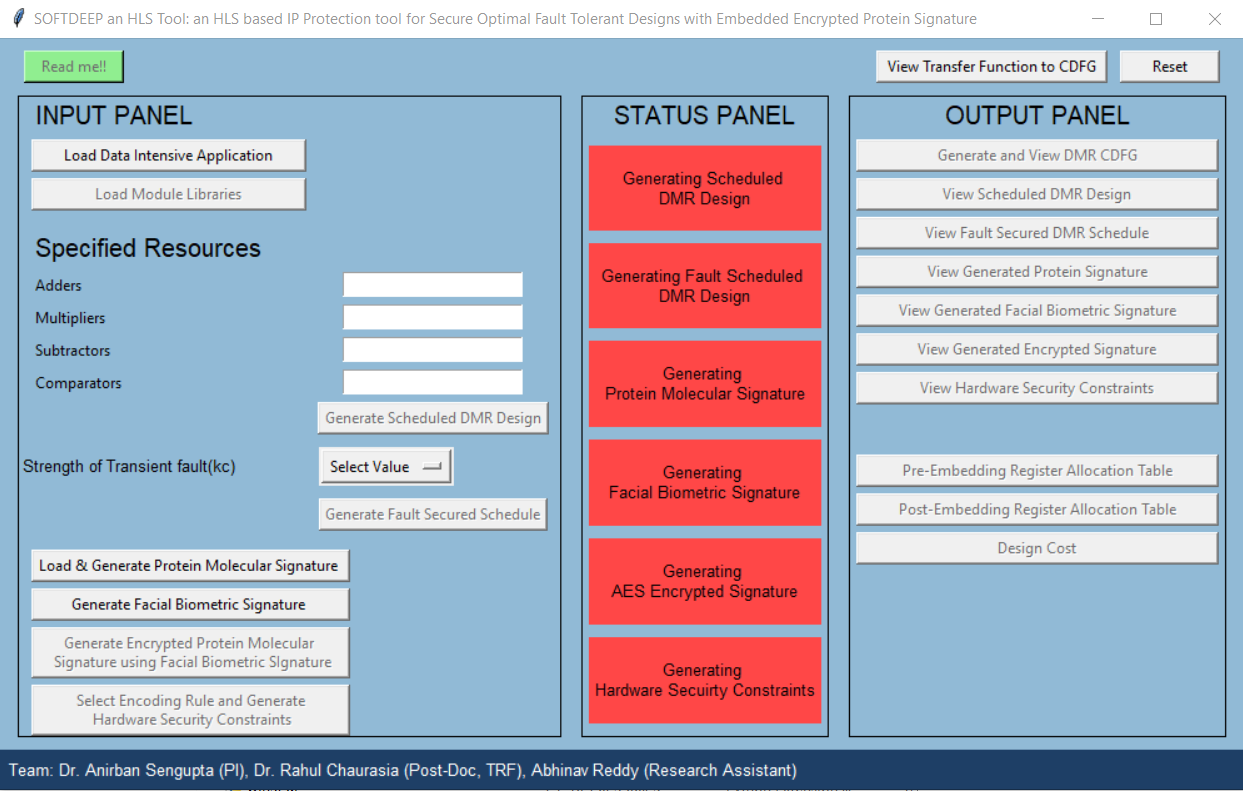
5998



5998
Download Section (Free/Publicly available):- Hardware Security Tools for Hardware Accelerators/ IP cores
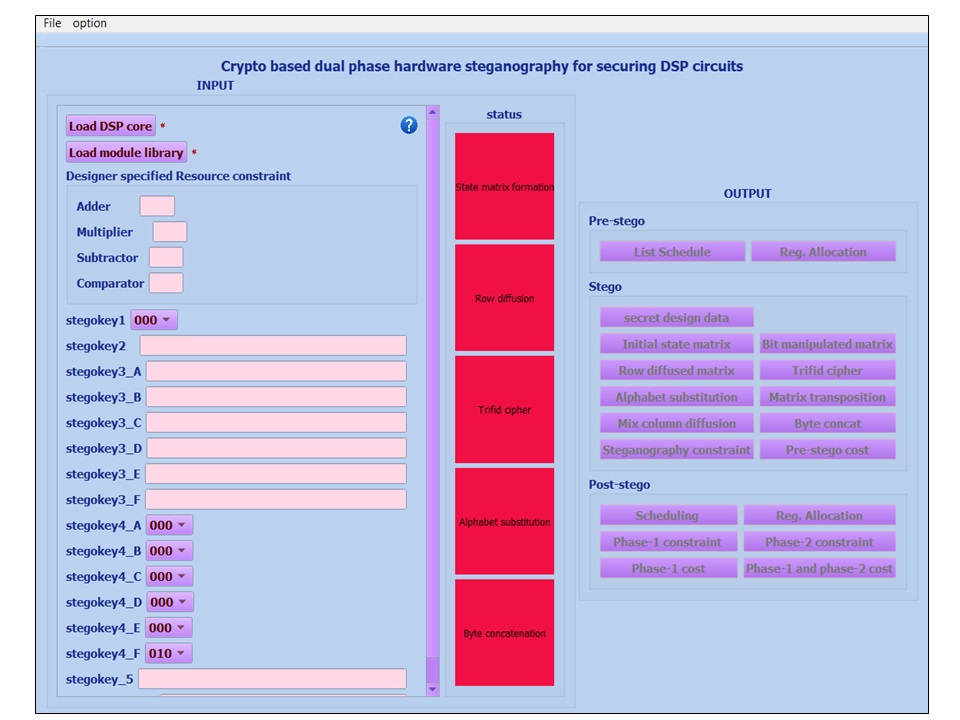
(3) Crypto-stego tool -: Crypto-steganography tool Click here for tool download
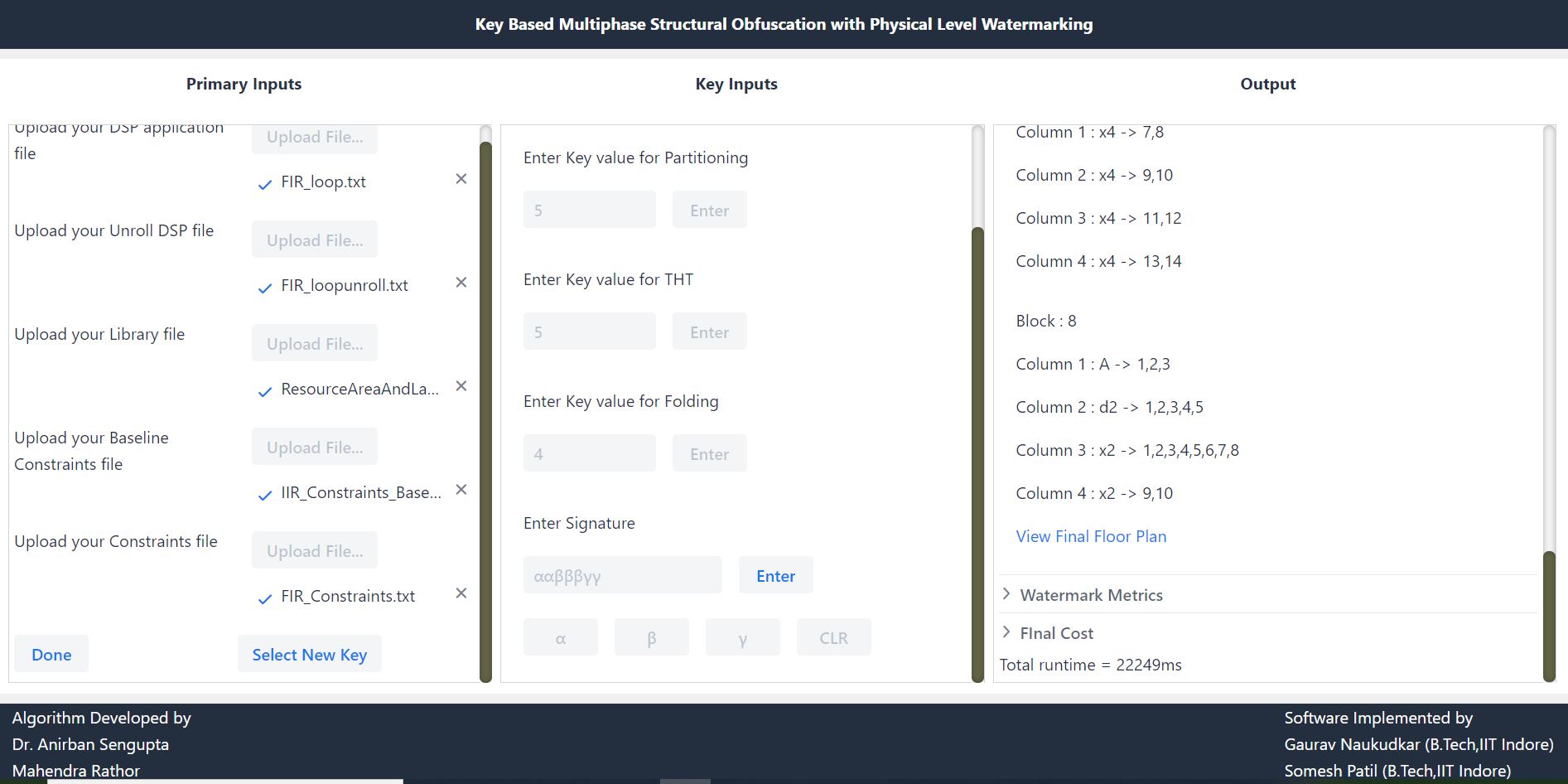
(5) KSO-PW tool -: Key-driven structural obfuscation and physical level watermarking tool Click here for tool download